HSE Omicron SMS Spoofing - Investigation

This morning, my Dad mentioned receiving a text from the HSE (Irish Health Service) about being a close contact of a confirmed Omicron case. Our first thoughts were that this seemed relatively familiar as we are still living with the virus. To be fair to Dad, I have him well trained in the arts of SMS spoofing and he was not convinced it was legitimate just because the text was appearing in the same message thread as a legitimate vaccine booster notification he had previously received from the HSE. So he asked me to have a look, here's the text:
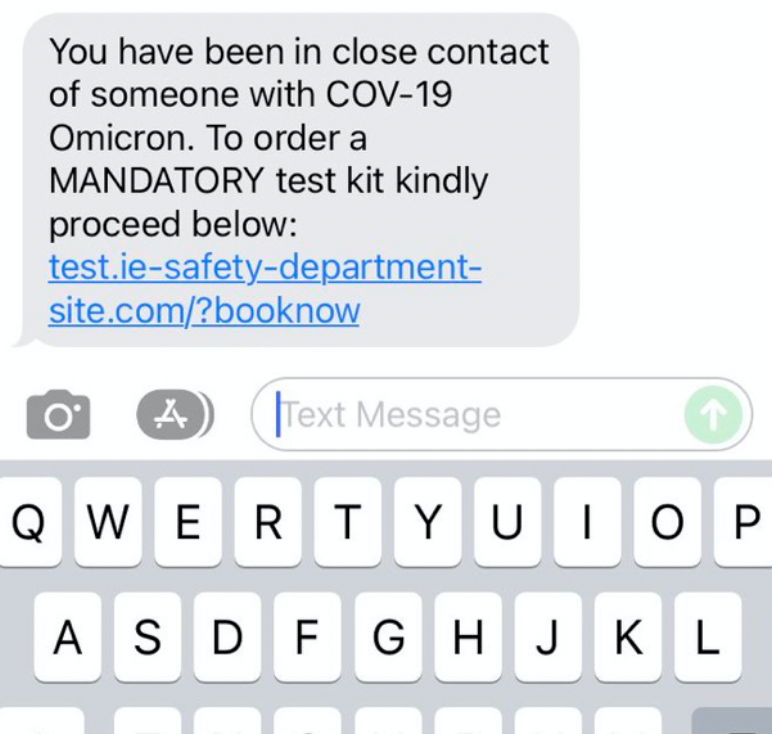
I really scrutinise the language of these things, sometimes to a fault but always with the intent of being overly cautious. In this case, I noticed three red flags in the language, the tone and the domain:
- The historic (legitimate) text uses "COVID-19" whereas this new suspicious text says "COV-19" which may have been nothing, but the inconsistency just stuck out to me, the norm is COVID-19 and this would have been a flag even without an older text in the thread.
- The "MANDATORY" in all caps was unnecessary. The word naturally instills a sense of urgency without having to be capitalised.
- The URL, my immediate reflex with URLs is to run them through the URL scanner on virustotal.com to see if anything gets flagged. For me, this is a fast way of triaging a link for anything obvious, but it is never to be used to determine if a URL is completely risk free, especially if the URL doesn't even have the domain name like this one. We would expect to see the HSE domain in there, somewhere at least.
So, the link does not appear to do anything suspicious off the bat, good.
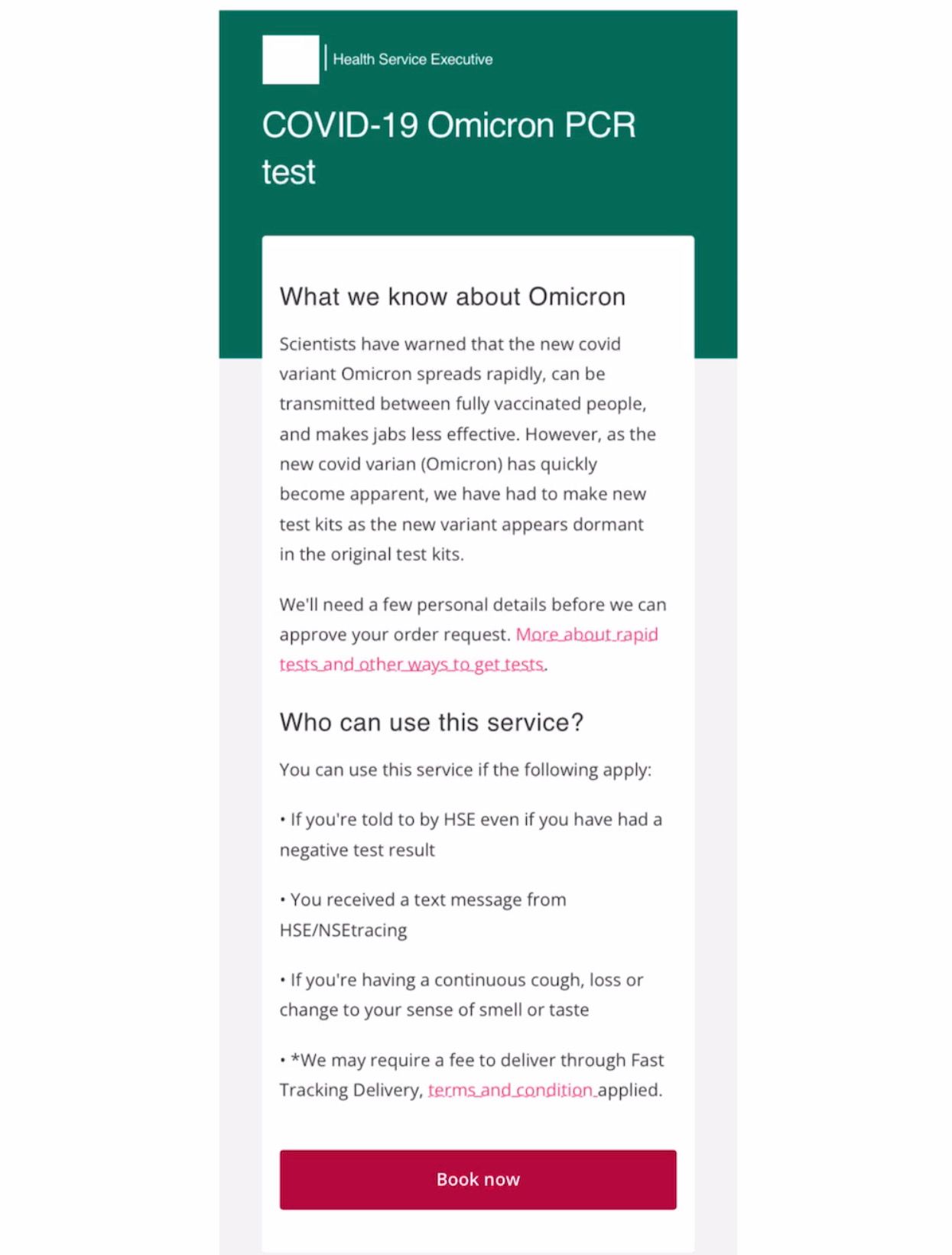
Next, I sent myself the text so I could investigate the URL on a test device. Opening the URL presents you with the below page, listing generic information (with odd language) and a "terms and condition" URL to some outdated HSE "Terms for Service & Supplies" document from January 2013.
At the bottom, there's a book now button which takes you to a page with standard form to collect your personal details:
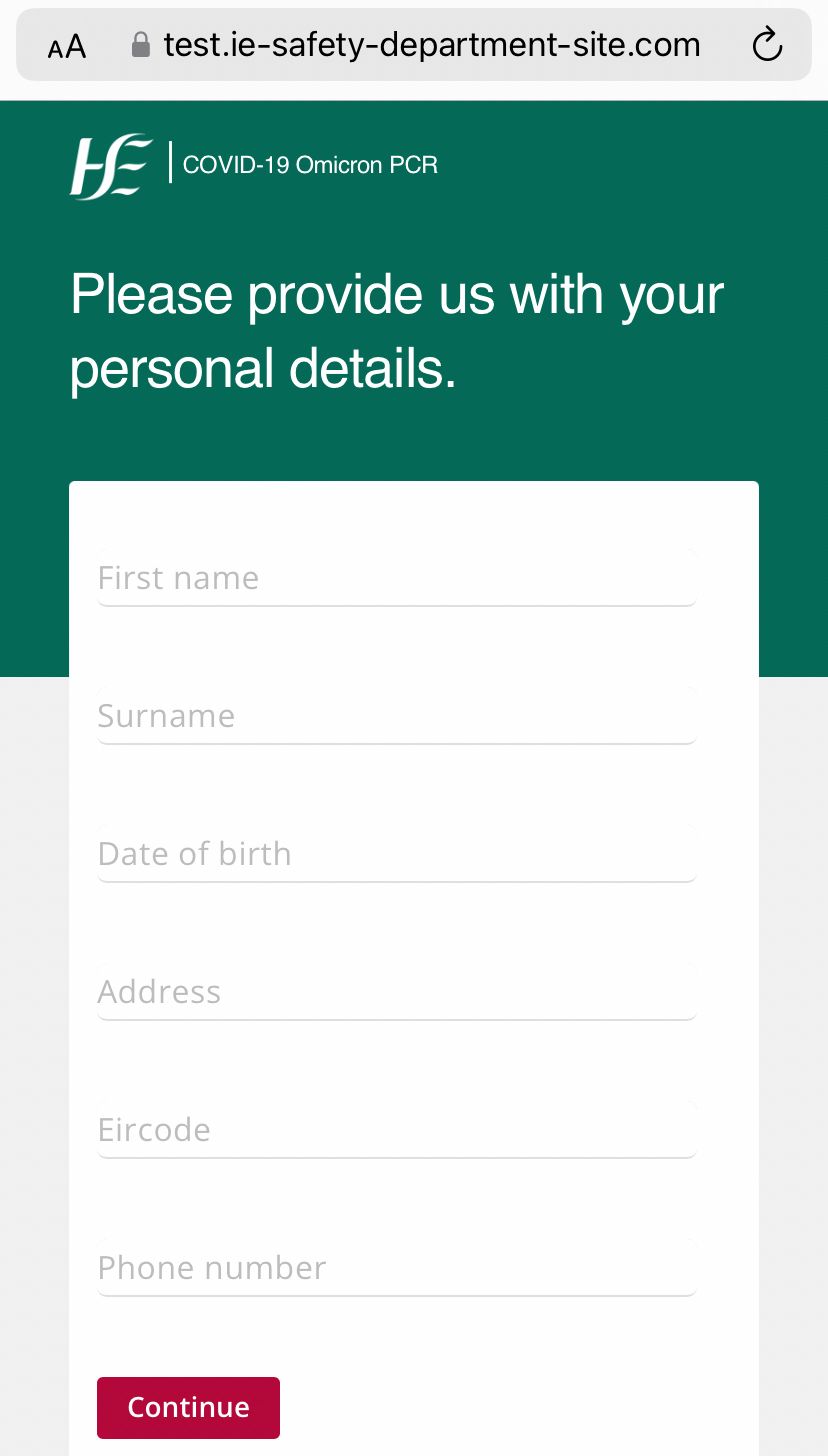
Immediately I found this odd as the HSE should have all of this already, not to mention after the HSE cyber attack in May 2021 I wouldn't be surprised if it was now publicly available data. At this point, I'm confident it's a scam and so I decided to be cheeky and just clicked continue while leaving the form blank.
SUCCESS! Even Dad was confident this page was a huge red flag:
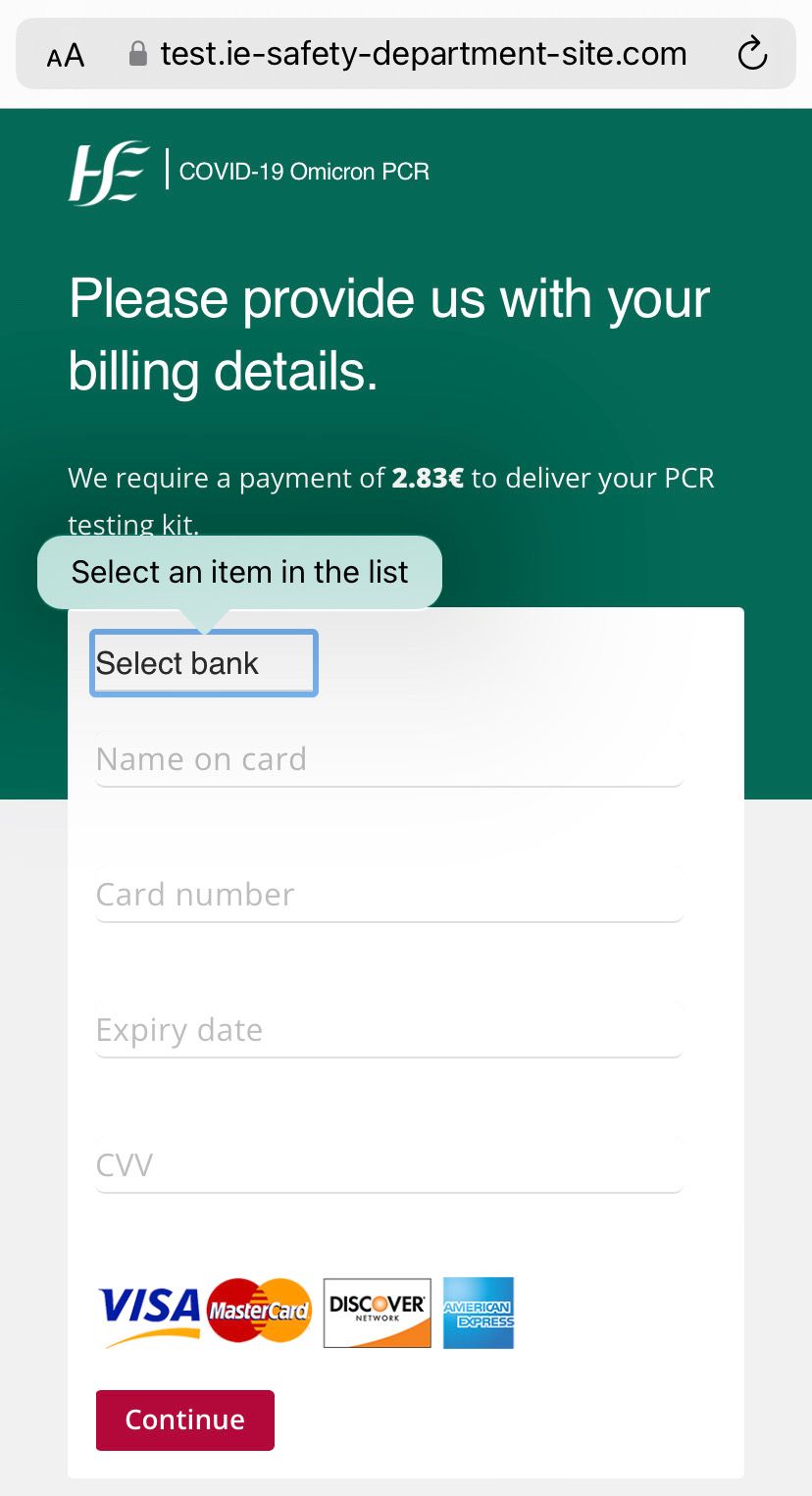
This justification for payment has been around a long time now and really gained popularity with attackers during lockdown with the increase in online shopping and thus people getting used to customs and delivery fees. Bundle that perception with the fact that it's a small sum of money and it's believable for many.
I was curious as to how strong the scammers development skills were so I decided to be cheeky (again) and try submit the form blank and to my surprise, it forces you to choose a bank from the dropdown:
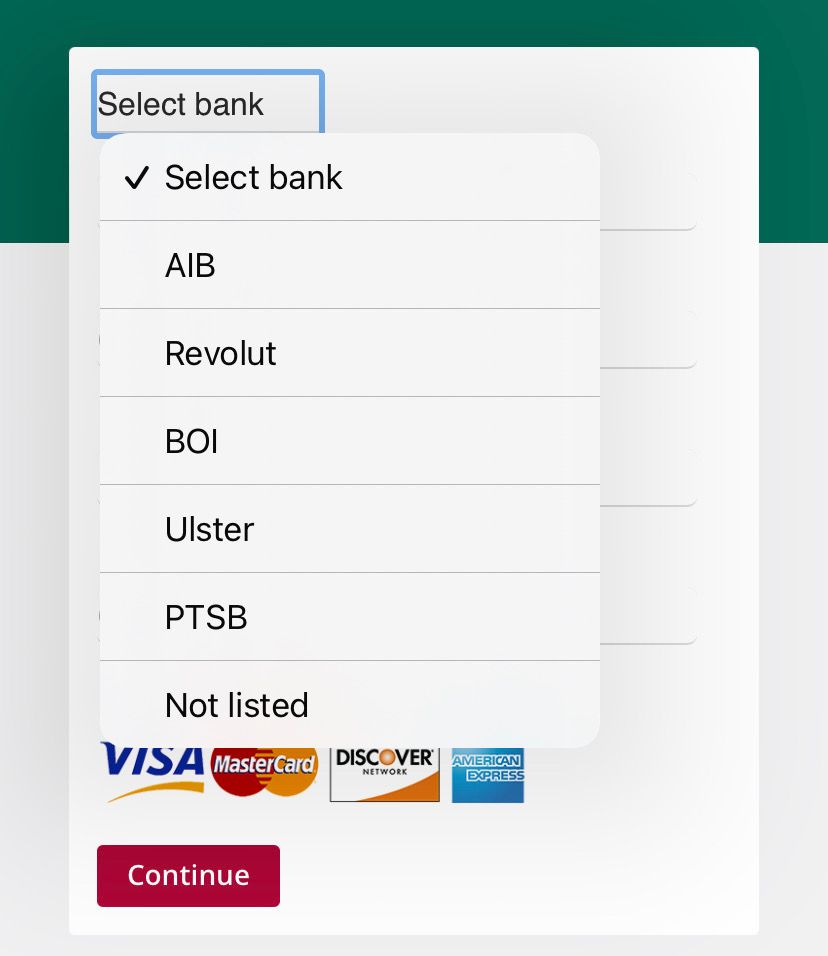
Thankfully for us, the scammers have provided an option for "Not listed" which I then selected and re-submitted the remaining blank form. SUCCESS!
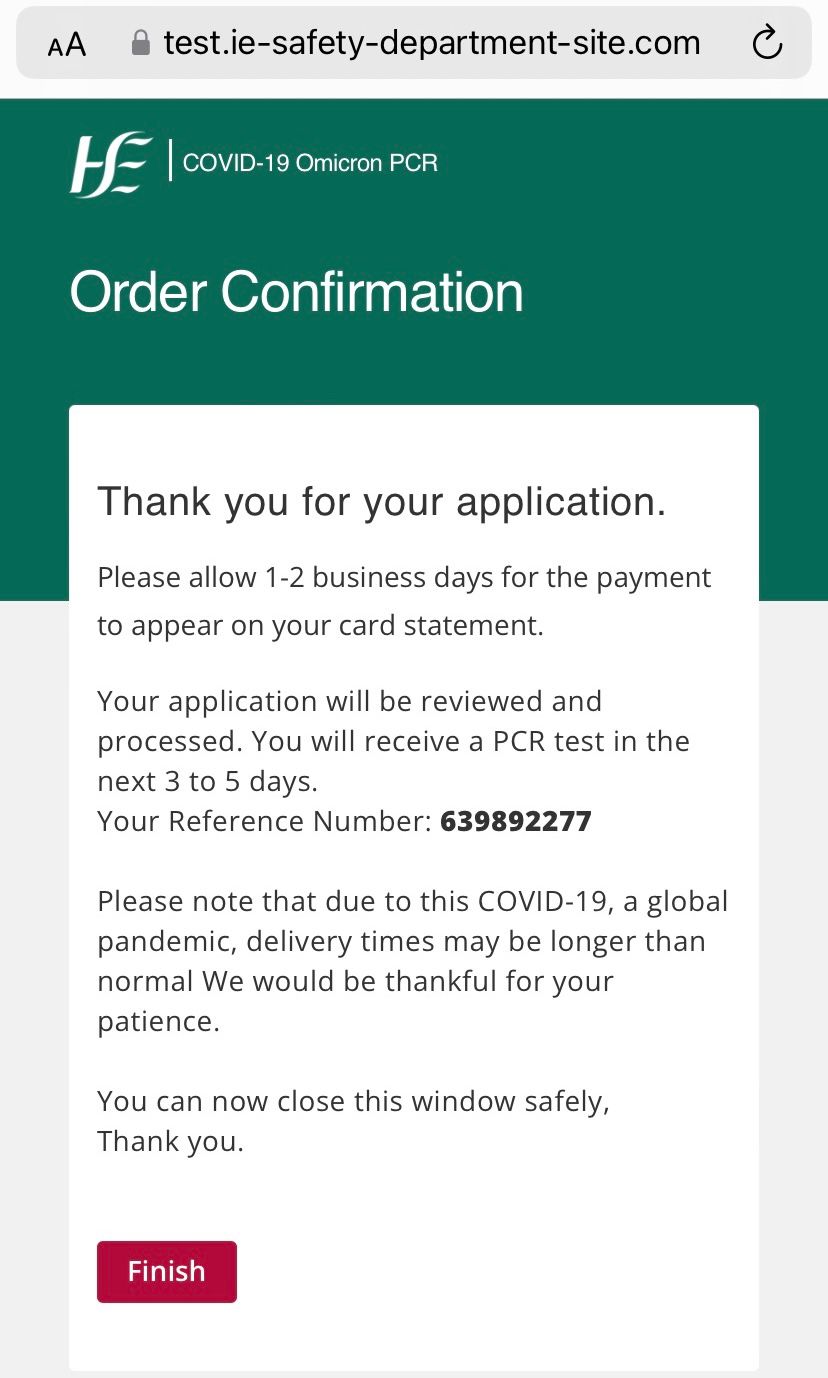
I even got a reference number! (after testing a second time the reference number does appear to be different, although I can't fathom as to why. At best they're used as a way of distinguishing multiple victims bank details once captured). There's also a delivery estimate of 3-5 days even though I gave no address.
All of this evidence points to this being a smishing attack in an attempt to harvest banking card details. The logic is there to harvest the data but there is no checks in place to ensure it is at all accurate.
Update 15/09/22 @ 20:16: the site now appears to be offline after redirecting to the legitimate HSE site for a few hours.
Summary
Phishing attacks of all kinds are designed to trick you into disclosing sensitive information. Always look out for red flags such as:
- Urgent, threatening or authoritative language.
- Requests for sensitive information
- Any URLs (especially misspelled domains)
- File attachments in emails.
- Poor grammar.
If you enjoyed this post, please consider supporting my work through the button below or becoming a free subscriber, it really helps, thank you!
If you're a business and would like to discuss consulting services, you can request a free consultation here: https://www.megabytesandme.com/services/
Thank you!
